Internal SIEM vs. External SIEM
Understanding Host-Based Vs. Network Based Cybersecurity Threats
Security Incident Event Management (SIEM) is a saturated industry with over 30 notable businesses specializing in the correlation of Cybersecurity threat analytics, but only one of those companies focus on Host-Based devices rather than Network-Based events. The problem for industry is insatiable rise of Hackers and that they have proven that they are skilled as they continuously usurp the current “Tech-Stack” of modern Cybersecurity tools, services, and protections, used by Mid-Market Corporations and Enterprises today.
Proof is everywhere and everyone has heard about breaches where technical adversaries have gained “UNAUTHORIZED PRIVILEGED ACCOUNT ESCALATION,” but the public generally learns of these breaches after they have been publicly disclosed. These types of headlines happen everywhere and are far too frequent for anyone to feel cyber-safe or comfortable. But what if there was an actual process for stopping hackers in One-Move, which was based upon objective-based events and forensic artifacts?
Compare SIEM Solutions: Host-Based ANAMO CDM vs. System-Based Splunk
ANAMO CDM is a highly specialized, host-based Continuous Diagnostics and Mitigation (CDM) platform that uses advanced comparative HashID Analytics which continuously identifies a broad range of forensic evidence in near real-time to deliver its version of SIEM. Splunk is a broad, system-agnostic SIEM solution requiring the mass collection of logs and highly curated rules to subjectively identify anomalous behaviors. The primary difference lies in their scope: ANAMO focuses internally on deep, real-time analysis of individual host risks and vulnerabilities over Operation Technology (OT) and Internet Technology (IT) devices, whereas Splunk collects and correlates network-based which amount to volumes of comprehensive log data from across the entire system or enterprise. To simplify, the following breakdown highlights the most obvious attributes of both, of course other remain.
Products |
ANAMO |
Splunk |
| Primary Focus | Deep, host-level internal-system monitoring, risk assessment, eDiscovery, mitigation, and reporting designed to eliminate Unauthorized Privileged Account Escalation and CVE mitigation. | Broad, enterprise-wide external-system security monitoring, data analysis, and reporting designed for data archival and parsing of Logs to identify standard parameters and inconsistencies of rule-based security risks. |
| Data Collection | “Log-less” agent-based data collection harnesses Comparative HashID analytics for continuous risk assessment of transactions, users, ports, permissions, and software vulnerabilities to the Kernel level. | Gathers and indexes machine-generated data Logs from virtually any source, including firewalls, servers, applications, and endpoints. |
| Key Capability | Visualizing Real-time identification of adversary activities, Indicators or Attack (IoA’s), zero-day exploits, and system modifications on endpoints using autonomous machine learning. | Uses its Search Processing Language (SPL) and machine learning for searching, analyzing, and visualizing large volumes of data.
Provides clarity to Indicators of Compromise (IoC’s) |
| Alerting | No-Delay real-time alerts on suspicious activities such as unauthorized changes or pivots on a host. | Creates alerts based on scheduled searches and predefined rules, which may introduce delays compared to ANAMO’s real-time capabilities. |
| Architecture | A patent-pending CDM platform that delivers deep, host-centric visibility without log parsing or need for massive storage, offered as a SaaS product or licensing agreement. | A scalable data platform with a forwarder/indexer/search head architecture for on-premises, cloud, or hybrid deployment. |
| Strengths | Low cost and complexity for deployment
Used with IT or OT Devices, on Windows or Linux OS’s, it continuously interrogates systems autonomous to eliminate the Dwell-time of an adversary. Delivers deep internal host insights. Tracks and correlates users, permissions, ports, as well as software (CVE) vulnerabilities at the host or enterprise level. Proactive threat hunting: Identifies bad actors and insider threats by monitoring and reporting upon unusual and nuanced endpoint activity. Database of forensic artifacts |
Enterprise-scale visibility: Provides a centralized view of security events across an entire IT infrastructure.
Broad integration: Flexible platform with numerous apps and add-ons for data ingestion and integration. Ability to add, change or delete log parsing rules Centralized log repository |
| Limitations | Limited systemic view: Less focused on correlating events across the entire network or from external data sources.
Does not monitor outside of the Host |
High cost and complexity: Can be expensive and resource-intensive to deploy and manage at enterprise scale. Delayed alerts: Can have potential visibility gaps for fast-moving threats due to its reliance on scheduled searches. Does not monitor inside the Host |
| Compliance | Enhances Zero Trust Architecture (ZTA) and supports federal compliance, including CMMC, NIST 800 and HIPAA. | Used widely for compliance reporting across various industries due to its extensive data aggregation and reporting capabilities. |
Which is right for your needs?
Your choice between ANAMO CDM and Splunk depends on your organization’s security technical capabilities, posture, goals, and budget.
Choose ANAMO if:
- You seek rapid identification of internal host-based threats based upon objective facts from forensic artifacts in near real-time
- You need to focus on deep, real-time monitoring and mitigation of threats across Operational Technology (OT) and Internet Technologies (IT) specifically at the host level across Open-Systems and Operating Systems such as Linux or Windows.
- Your priority is to proactively identify insider threats, target file paths, zero-day exploits, and lateral movement by malicious actors within endpoints.
- Your environment requires an easily managed SIEM which is financially affordable, offers strong Cybersecurity capabilities, and can also achieve advance security and monitoring requirements for compliance with federal frameworks like NIST.
Choose Splunk if:
- You need a centralized platform to collect logs and analyze machine data from a wide variety of sources across a large, complex IT environment.
- Your security operations require the collection of logs or correlating logs from network devices, servers, and applications to get an enterprise-wide view of security events.
- Your organization needs flexible data management and powerful search capabilities for both security and operational intelligence use cases.
In many cases, organizations choose to integrate specialized host-based solutions like ANAMO with broader SIEMs like Splunk to achieve comprehensive security. The host-based tool provides granular, real-time endpoint threat detection, while the system-based SIEM offers holistic, enterprise-wide analysis and compliance reporting
The Deeper Dive: Log Parsing vs. Comparative HashID Analytics
The primary difference in real-time alerting between ANAMO CDM and Splunk lies in their focus, source of data, and method of detection. ANAMO provides deeper, agent-based alerts focused on host-centric anomalies, while Splunk offers broad, customizable alerts based on log data from across the enterprise. The best approach for many organizations is to use a combination of both.
ANAMO CDM: Host-centric and predictive
ANAMO’s alerting is designed for identifying and responding to threats at the endpoint level, with a focus on mitigating the threat dwell time.
- Data source: ANAMO uses a lightweight, “log-less” agent on open systems such as a Host or Server to collect and analyze data directly from endpoints. It continuously monitors key indicators like user permissions, network ports, and file systems, rather than simply parsing logs.
- Detection method: It builds, monitors, and alerts upon modifications to the HashID of any system where Anamo is installed. It uses machine learning and generative AI to establish a baseline of normal host behavior. This allows it to proactively identify and alert on suspicious deviations, such as an authorized user making unauthorized changes or a zero-day exploit attempting to run.
- Alerting speed: The alerts are generated in near real-time because the analysis is performed directly on the host data as it is collected. The goal is to notify security teams immediately about threats like lateral movement or privilege escalation.
- Context: Alerts from ANAMO are highly contextualized for the host. They can flag specific users, groups, or software vulnerabilities that are associated with malicious activity.
- Key alerts:
- Insider threats: Abnormal behavior from an authorized user, such as Permission or Port modifications or accessing sensitive directories.
- Zero-day exploits: Anomalous behavior that indicates a new, unknown exploit, cross-referenced with CVEs and port changes combined with User behavior.
- Adversary pivoting: Real-time tracking of unauthorized credential changes or movement across the system, associations to groups, or access to File paths.
Splunk: System-wide and customizable
Splunk’s alerting is built on its capability to ingest, index, and search massive volumes of machine-generated data from any source across the enterprise.
- Data source: Splunk’s alerts are based on data from closed systems such as network devices, servers, applications, and endpoints. The data is collected by forwarders, sent to indexers, and then searched.
- Detection method: Alerts are triggered by a saved search that runs either on a schedule or continuously in real-time. Security analysts can create a wide range of custom alerts using Splunk’s Search Processing Language (SPL) to look for specific event patterns.
- Alerting speed: Splunk offers both scheduled and continuous real-time searches.
- Scheduled alerts are resource-efficient but introduce a delay. For example, a search that runs every 15 minutes will only detect an incident after the next scheduled search.
- Continuous real-time searches provide a faster response but are resource-intensive, making them impractical for monitoring a markedly high volume of data.
- Context: Splunk alerts benefit from a broader, enterprise-wide context. They can correlate events across many different systems, such as a failed login on a server combined with firewall alerts. However, the data can be voluminous and require more analysis to pinpoint the root cause on a specific host.
- Key alerts:
- Failed logins: A specified number of failed logins on a server within a certain time window.
- Access anomalies: An account accessing a resource from an unusual IP address or at an unusual time.
- Vulnerability scans: Alerts generated when a vulnerability scanner logs a critical finding.
Combining ANAMO CDM and Splunk for a robust defense
For maximum security, organizations can integrate ANAMO with a SIEM like Splunk to achieve both deep host-level and broad system-level visibility.
- ANAMO detects and alerts on internal host-level threats in real-time, such as insider activity or zero-day exploits, providing immediate, granular insight.
- ANAMO data is sent to Splunk to be correlated with other enterprise-wide security events from firewalls, network infrastructure, and other devices.
- Splunk provides the holistic view, allowing security teams to see if an ANAMO alert on a single host is part of a larger, enterprise-wide attack.
- Together, they enable faster and more informed threat response. The combination provides deep, forensic-level detail from ANAMO, alongside the broad, customizable alerting and reporting capabilities of Splunk.
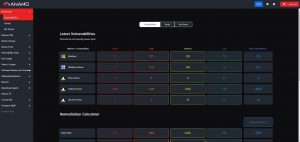
What does Internal, Host-Based, Continuous Diagnostics & Mitigation SIEM Look Like?
Below: Screenshot of Anamo’s active CVE dashboard which without any effort or scheduling, autonomously interrogates all Transactions, Permissions, Users, CVEs, and Forensic Modifications of Internet Technology (IT) devices and Operational Technology (OT) devices, on both Windows and Linux Operating Systems:
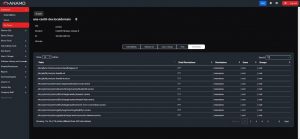
Question: Who might have “777” or “WRX*** Privileged Accounts on any system across an entire Enterprise at any moment, and what is the correlated System and File Path which is associated to each Permission?
Below: Screenshot of Anamo’s Permission Modification dashboard which without any effort or scheduling, autonomously interrogates all Transactions, Permissions, Ports, Users, Groups, and associated Forensic Modifications of Internet Technology (IT) devices and Operational Technology (OT) devices, on both Windows and Linux Operating Systems:
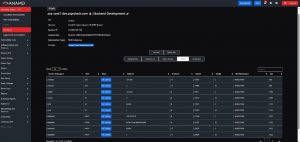
Question: Across an entire Enterprise of IT and OT systems; Could automated SOC Notifications of any Port-Modification direct User-Session-Termination before Data Exfiltration transmission could begin?
Below: Screenshot of Anamo’s Port investigation dashboard which without any effort or scheduling, it autonomously interrogates all Ports and Transactions and gathers Forensic data on all Host-Based systems. Data points which are Continuously Monitored and Alerted upon, including: The Port, Service On Port, Address, Protocol, Socket, Family, Net Namespace, PID and more, as shown:
To Schedule a Demonstration or for More Information: Contact Anamo.io