The 7 Essential Steps of the Cybersecurity Kill-Chain Process
Nearly 1 Billion Individual Records / Hacked
900,833,392+ Records Breached During 5,063 Reported Data Breaches*
Solution: Implementing the 7 Essential Steps of the Cybersecurity Kill-Chain Process
“Implementing this Kill-Chain Will Stop Your Enemy Cold” says Goetsch, CEO of US ProTech, a Cybersecurity expert since 1999. But he adds “Do Not Kill Them before Gathering the Highly Prized Intelligence you want.”
US ProTech has Mastered the Cybersecurity Kill Chain framework 1st developed with the DOD. It’s part of a process we like to call the Intelligence Driven Defense model for the identification and prevention of cybersecurity intrusion activity. The model identifies what 7-steps the adversaries must complete in order to achieve their objective and more importantly how and when to kill their presence.
In this series of 4 emails, you will gain the critical info needed to take action against the greatest threat of our time – Hackers using APT’s to devastate governments and businesses with ZDE’s.
The 7 Essential Steps of the Cybersecurity Kill-Chain Process
Step 1: RECONNAISSANCE
- Harvesting email addresses, conference information, etc.
- The first step of any APT attack is to select a target. Depending on the motive(s) of the APT actor, the victim could be any company or person with information the attacker(s) sees as valuable. Attackers “fingerprint” the target to create a blueprint of IT systems, organizational structure, relationships, or affiliations and search for vulnerabilities—both technical and human— to exploit and breach the network. As large organizations tend to invest in multiple layers of security, this step could take weeks, even months. However, the more knowledge the APT actor acquires on its target, the higher the success rate of breaching the network.
Step 2: WEAPONIZATION
- Coupling exploit with backdoor into deliverable payload
- Next, attackers will re-engineer some core malware to suit their purposes using sophisticated techniques. Depending on the needs and abilities of the attacker, the malware may exploit previously unknown vulnerabilities, aka “zero-day” exploits, or some combination of vulnerabilities, to quietly defeat a network’s defenses. By reengineering the malware, attackers reduce the likelihood of detection by traditional security solutions. This process often involves embedding specially crafted malware into an otherwise benign or legitimate document, such as a press release or contract document, or hosting the malware on a compromised domain.
Step 3: DELIVERY
- The three most prevalent delivery vectors for weaponized payloads by APT actors, as observed by the US ProTech Computer Incident Response Team (USPT-CIRT) for the years 2005-215, are email attachments, websites, and removable media such as a USB stick. The transmission and delivery of weaponized bundles to the victim’s targeted environment is the objective but these efforts arrive with some digital fingerprinting. This stage represents the first and most important opportunity for defenders to block an operation; however, doing so defeats certain key capabilities and other highly prized data. At this stage we measure of effectiveness of the fractional intrusion attempts that are blocked at the delivery point.
Step 4: EXPLOITATION
- At this stage exploiting a vulnerability to execute code on victim’s system command channel for remote manipulation of victim is the objective. Here traditional hardening measures add resiliency, but custom defense capabilities are necessary to stop zero-day exploits at this stage. After the weapon is delivered to victim host, exploitation triggers intruders’ code. Most often, exploitation targets an application or operating system vulnerability, but it could also more simply exploit the users themselves or leverage an operating system feature that auto-executes code. In recent years this has become an area of expertise in the hacking community which is often demonstrated at events such as Blackhat, Defcon and the like.
Step 5: INSTALLATION
- At this stage the installation of a remote access Trojan or backdoor on the victim system allows the adversary to maintain persistence inside the environment. Installing malware on the asset requires end-user participation by unknowingly enabling the malicious code. Taking action at this point can be considered critical. One method to effect this would be to deploy a HIPS (Host-Based Intrusion Prevention System) to alert or block on common installation paths, e.g. NSA Job, RECYCLER. It’s critical to understand if malware requires administrator privileges or only user to execute the objective. Defenders must understand endpoint process auditing to discover abnormal file creations. They need to be able to compile time of malware to determine if it is old or new. Answers to the following questions should be consider mandatory: How does it last, survive, etc. Does it use Auto run key, etc. Does Backdoor need to run to provide access. Can you identify any certificates and extract any signed executables?
Step 6: COMMAND AND CONTROL
- This stage is the defender’s “last best chance” to block the operation: by blocking the Command and Control channel. If adversaries can’t issue commands, defenders can prevent impact. Typically, compromised hosts must beacon outbound to an Internet controller server to establish a Command & Control (aka C2) channel. APT malware especially requires manual interaction rather than conduct activity automatically. Once the C2 channel establishes, intruders effectively have “hands on the keyboard” access inside the target environment. Let’s remember that seldom is Malware automated, normally this command channel is manual. The general practice of intruders is: Email – in, Web = Out. The trick for them is to have established the control over many work stations in an effort to “exfiltrate” data without setting off any anomalies or other monitoring applications based upon content, quantity, frequency, etc. Hence, the reason it is essential to have the proper tools in place that can identify, track, observe, stop and destroy these campaigns within your arsenal of capabilities.
Step 7: Actions on Objectives
- The longer an adversary has this level of access, the greater the impact. Defenders must detect this stage as quickly as possible and deploy tools which will enable them to collect forensic evidence. One example would include network packet captures, for damage assessment. Only now, after progressing through the first six phases, can intruders take actions to achieve their original objectives. Typically, the objective of data exfiltration involves collecting, encrypting and extracting information from the victim(s) environment; violations of data integrity or availability are potential objectives as well. Alternatively, and most commonly, the intruder may only desire access to the initial victim box for use as a hop point to compromise additional systems and move laterally inside the network. Once this stage is identified within an environment, the implementation of prepared reaction plans must be initiated. At a minimum, the plan should include a comprehensive communication plan, detailed evidence must be elevated to the highest ranking official or governing Board, the deployment of end-point security tools to block data loss and preparation for briefing a CIRT Team. Having these resources well established in advance is a “MUST” in today’s quickly evolving landscape of cybersecurity threats.
REAL LIFE EXAMPLE:
A Watering Hole Attack on Aerospace Firm
Exploits CVE-2015-5122 to Install IsSpace Backdoor
Case Study:
On July 16, 2015, the Palo Alto Networks Unit 42 threat intelligence team discovered a watering hole attack on the website of a well-known aerospace firm. The website was compromised to launch an apparent watering-hole attack against the company’s customers. It was hosting an Adobe Flash exploit targeting one of the newly disclosed vulnerabilities from the Hacking Team data breach, CVE-2015-5122. This attack yet again showcases the opportunistic tendencies of adversary groups and bad actors. The malware deployed by this exploit has been seen in a number of targeted attacks and provides attackers with a foothold on the victim’s machine and/or network. The exploit file, movie.swf, was ZWS compressed, a tactic that has been observed to evade anti-virus programs. Once uncompressed, a binary was found to be embedded in the Flash file. Upon further analysis, this file was found to contain behavior consistent with a Trojan commonly called IsSpace. Based on its codebase and behavioral patterns, it appears that IsSpace could possibly be an evolution of the NFlog backdoor, which has previously been attributed to the adversary groups DragonOK and Moafee. Both groups are thought to be operating out of Southeast Asia, and Moafee in particular has been associated with attacks on the US defense industrial base.
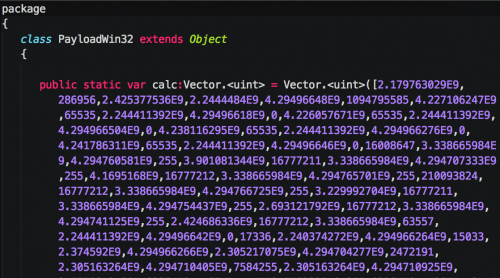
Exploit Details: The CVE-2015-5122 exploit found within the Flash file is nearly identical to the original proof of concept (POC) disclosed publicly from the Hacking Team data breach. An analysis by Trend Micro covers the POC in detail. Unlike the POC mentioned in the Trend Micro report, this particular exploit file was weaponized, and, instead of loading calc.exe, a much more malicious file was loaded. As seen in Figure 1, the embedded shellcode is obfuscated using the same technique of representing bytes as integers and exponential numbers. However, it appears that the adversary did not modify the POC much, as the variable name ‘calc’ remains unchanged.
