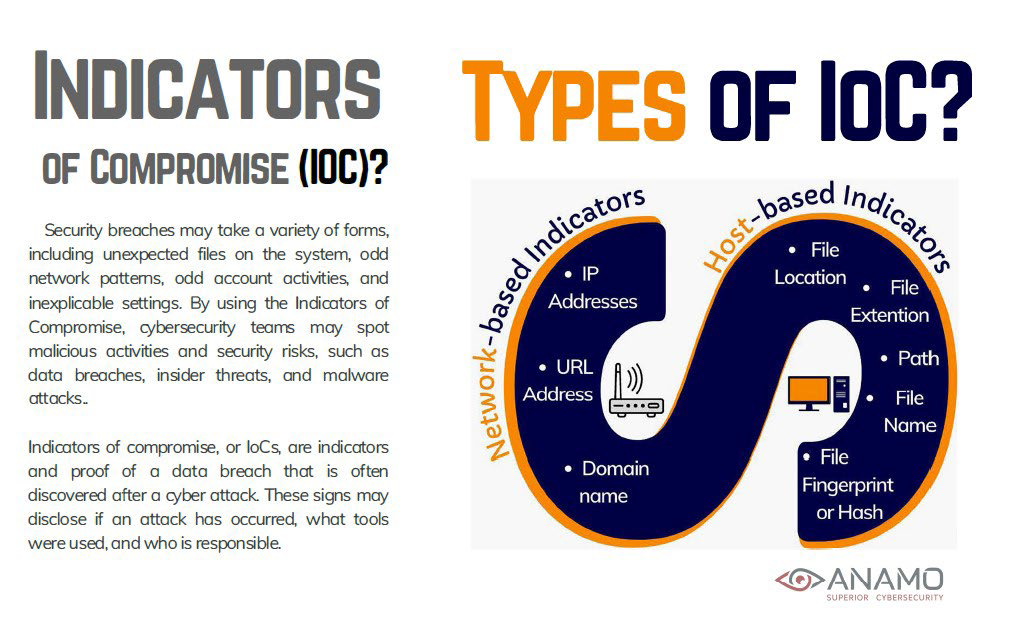
Indicators of Compromise (IoC)

In Cybersecurity, an Indicator of Compromise (IoC) is evidence suggesting a system or network may have been breached. US ProTech solves this by helping security teams identify and respond to potential or ongoing attacks, which is exactly what the Anamo CDM software offers as it correlates Host-Based Indicators of Compromise with comparative HashID Analytics, in Real-Time.
Clearly, businesses face a multifaceted cybersecurity landscape packed deeply with Technical Adversaries who seek to breach networks, elevate credentials, and exfiltrate the maximum value and Data possible. Targets include Intellectual Property, Assets, Personal Identifiable Information and much more. Tools and threats include Data Breaches, Ransomware, Unauthorized Privileged Escalation, Phishing Attacks, Command Injection, Buffer Overflow, Social Engineering, Malware, and the list goes on!
In March of 2025, we asked Technology Executives & Leaders the “Big Question.” They overwhelmingly stated that they have absolute needs, including:
1. Definitive evidence that something is happening, right now
2. To understand the significance and importance of the activity
3. Immediate identification where the activity is being presented
3. Having knowledge of options on how they need to respond
Solution: Having a system to deliver Cybersecurity IoC types in a CDM* format would be a Game-Changer. Anamo is today’s only commercial-grade Mid-Market CDM Cyber-tool!
Quote from a U.S. AIR FORCE GENERAL who conducted a “Capabilities Assessment”:
“Essentially, your (Anamo) software Agent correlates critical Host-Based Indicators of Compromise. It seems like the most effective process for delivering essential information. By using Anamo’s advanced comparative HashID Analytics, Cyber-practitioners are now capable of correlating data that has never been available before, Wow!” The concept of *Continuous Diagnostics and Mitigation (CDM) is over 10 years old with it’s origins dating back to 2013. Launched by CISA & DHS, today CDM is broadly used by over 300 Federal Agencies. Anamo is a phenomenal CDM product that should be considered, especially in the commercial market because it bridges significant attributes of SIEM, EDR, ASM, and other cyber-tools such as those gathering data forensics, delivery eDiscovery, and more.”
*CDM / The $8 Billion Dollar CISA/DHS Continuous Diagnostics & Mitigation Program
What CISA & DHS Say About CDM
What is ANAMO CDM?
✔ Anomalous Risk Detection of Internal System Indicators of Compromise (IoC’s)
✔ Autonomous Muti–OS Software CVE Interrogation/ API’s with NVD, CIRCL, SUSE
✔ Autonomous Endpoint Vulnerability Assessment and Tracking of User Behavior Risk
✔ Continuous Attack Surface Management Analysis Including OS, Package, & Kernel Level
✔ Continuous Tracking of Transaction, User, Group, Port, and Permission/ Add or Delete
✔ Diagnostics of Windows & Linux Operating Systems, Plus Software Inventory and History
✔ Diagnostics, Monitoring, and Alert Notification of all Collected Unique Hash ID Modifications
✔ Documentation and Inventory of System, System Hardware, UUID, and Transactions
✔ Real-Time Comparative Hash ID Analytics with Deep Cybersecurity Forensic Artifact Collection
✔ On-Demand eDiscovery and Reporting of related Systems and Cybersecurity Risk Information
✔ 100% Action and Mitigation Responsibility for Updates, Patches, Remediation (w/SOC+NOC)
Anamo is Autonomous & Continuous: Anamo bridges the very best attributes of today’s most advanced Cybersecurity tools and delivers the artifacts and alerts as logically correlated data, while providing Never–Before–Seen capabilities.
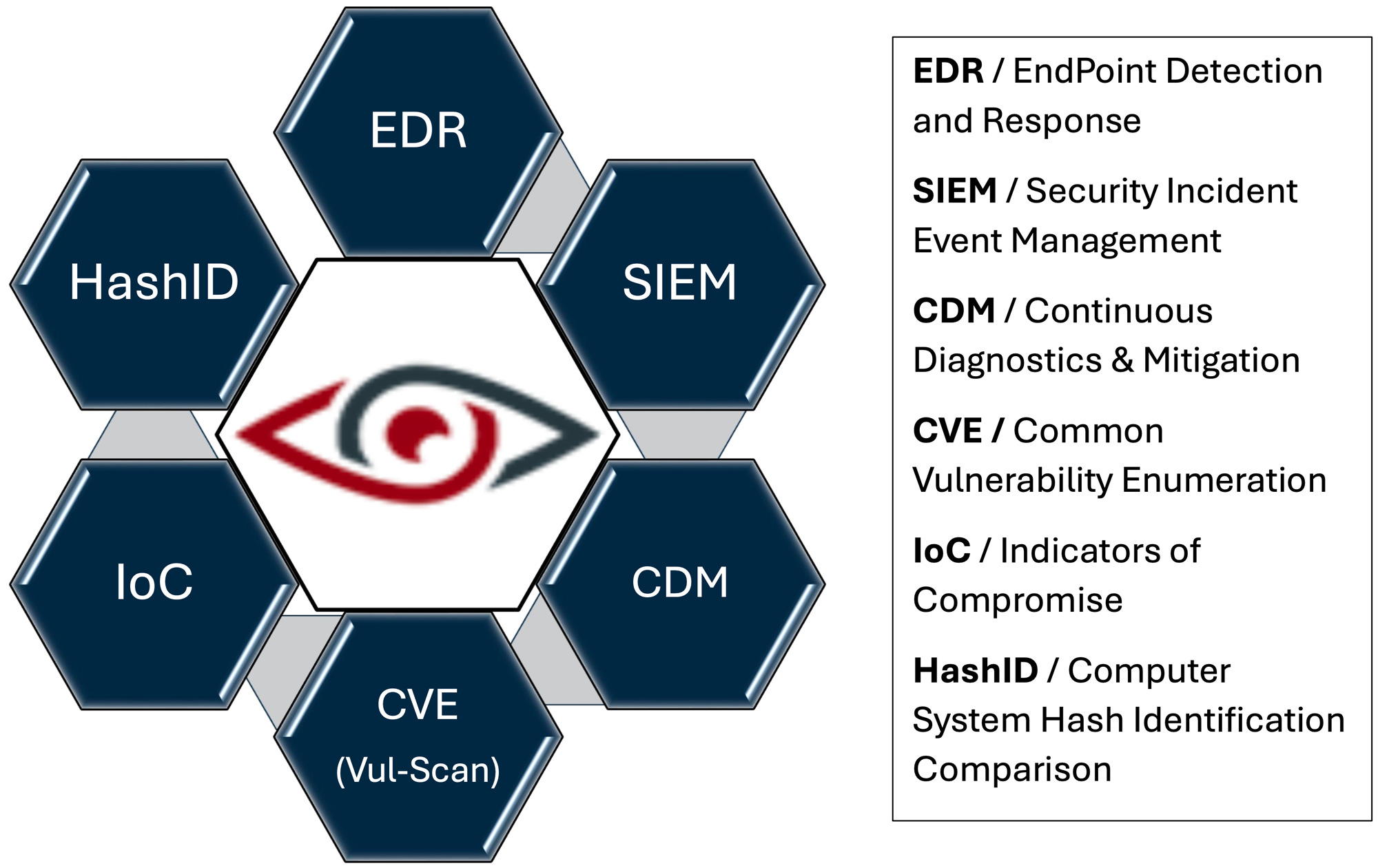
Anamo Supports a broad range of Cybersecurity practitioners who rely upon critical risk information being available ASAP. Because Anamo autonomously delivers continuous diagnostics, & mitigation (CDM) in real-time to active dashboards, Anamo has become the one essential platform to monitor and manage alert notifications because its patented technology tracks, collects, and cross-correlates essential cybersecurity forensics from previously disparaging data systems such those shown in the image above.
